Descripción
This plugin provides the functionality for Reflected XSS and Self-XSS.
For Reflected XSS, it checks the URL and redirects it if you enabled the Enable Blocking option and URL contains any Vulnerable code in it. It only block some parameters which are not allowed in URL and shown Block Parameters section. You can skip some of the parameters from it if you still like them to be used.
To provide more security, Prevent XSS Vulnerability also escape the HTML in the $_GET parameter which is commonly used to get parameters in PHP from the URL and print them in the HTML. This way, HTML properties will not work if anyone provided it in the URL.
There are many ways by which the plugin can be tested but it may varies for different sites according to their structure and development functionality.
Block Parameters
Prevent XSS Vulnerability block the following parameters in the URL if enabled from the Plugin Settings page.
- Opening Round Bracket
( - Closing Round Bracket
) - Less than Sign
< - Greater than Sign
> - Opening Square Bracket
[ - Closing Square Bracket
] - Opening Curly Bracket
{ - Pipe or Vertical Bar
| - Closing Curly Bracket
}
You can exclude any of the pre-defined parameter(s) or include any other parameter(s) from the Plugin Settings page.
Encode Parameters
Prevent XSS Vulnerability encode the following parameters in the URL if enabled from the Plugin Settings page.
- Exclamation Mark
! - Double Quotation
" - Single Quotation
' - Opening Round Bracket
( - Closing Round Bracket
) - Asterisk Sign
* - Less than Sign
< - Greater than Sign
> - Grave Accent "`
- Cap Sign
^ - Opening Square Bracket
[ - Closing Square Bracket
] - Opening Curly Bracket
{ - Pipe or Vertical Bar
| - Closing Curly Bracket
}
You can exclude any of the pre-defined parameter(s) to being encoded from the Plugin Settings page.
Escape HTML in `$_GET` Variable
Prevent XSS Vulnerability escape HTML in `$_GET` variable. `$_GET` variable is mostly used to put the values in HTML from the URL. This Check is quite useful if your site using/getting anything from the URL and printing it in HTML. It secures your Search and other sections as per your site functionality.
NOTE: Make sure to check your forms after activating the plugin and if you have woocommerce site then please also check the cart and checkout process.
Bug reports
Bug reports for Prevent XSS Vulnerability are welcomed on GitHub. Please note GitHub is not a support forum, and issues that aren’t properly qualified as bugs will be closed.
Capturas
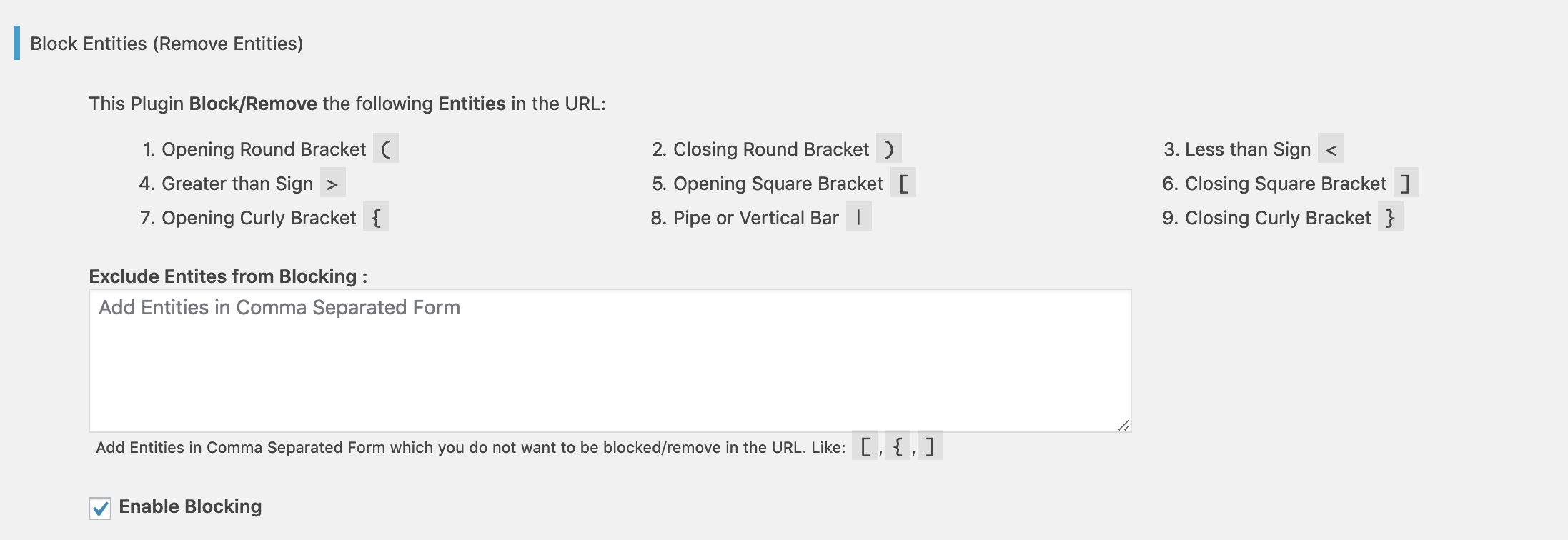
It removes the parameters from the URL which are used in XSS Attack and redirects the user (Recommended).
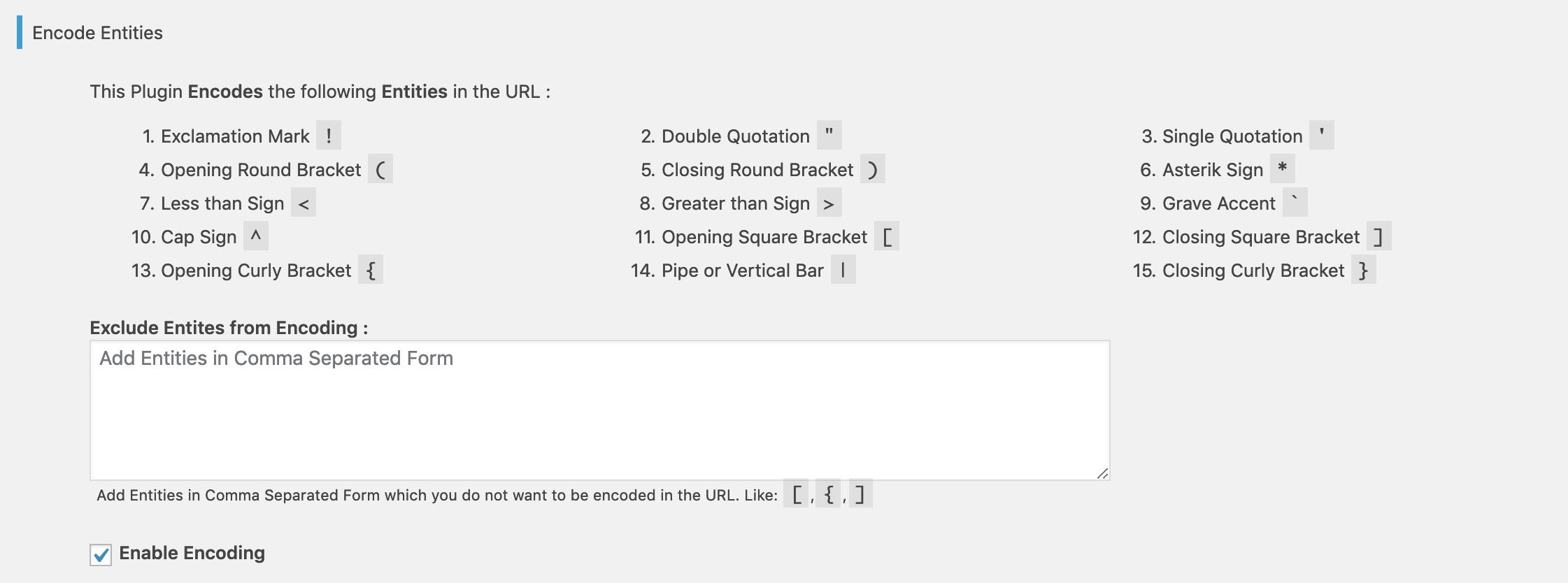
It encodes the parameters from the URL which are used in XSS Attack.
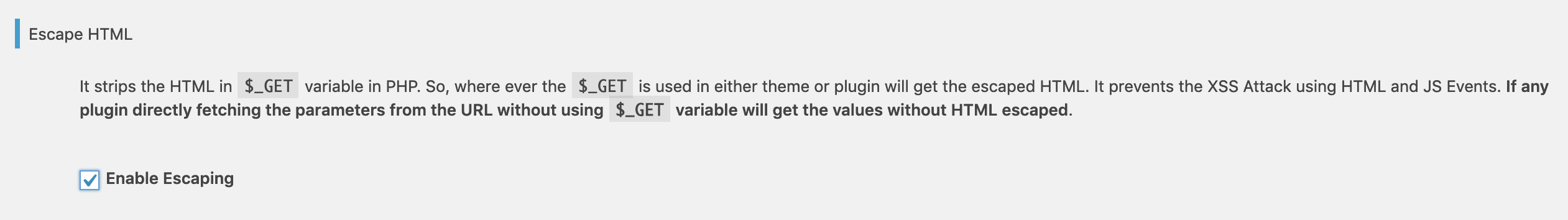
It escapes the HTML from the
$_GETPHP variable which is mostly used to read the data from the URL (Recommended).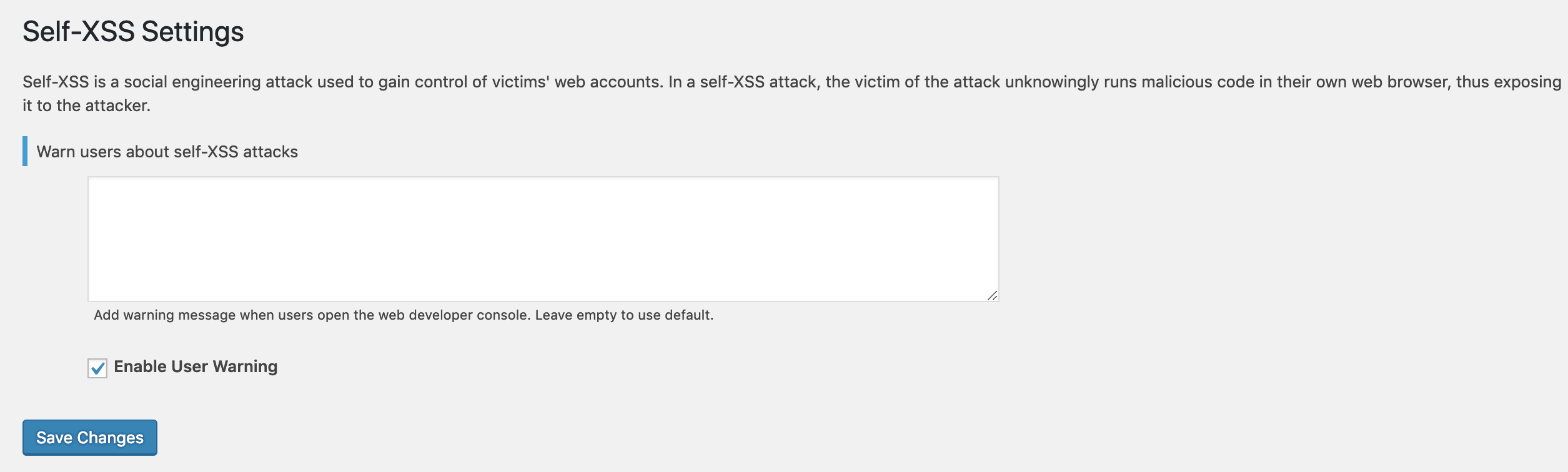
Add the message in developer console for the user to alert about the XSS attack.
Show message in developer console to alert user about the Self-XSS attack. This message can be customized from the settings page.
Instalación
This process defines you the steps to follow either you are installing through WordPress or Manually from FTP.
From within WordPress
- Visit 'Plugins > Add New'
- Search for Prevent XSS Vulnerability
- Activate Prevent XSS Vulnerability from your Plugins page.
- Go to "after activation" below.
Manually
- Upload the
prevent-xss-vulnerabilityfolder to the/wp-content/plugins/directory - Activate Prevent XSS Vulnerability through the 'Plugins' menu in WordPress
- Go to "after activation" below.
After activation
- Navigate to the
Prevent XSS Vulnerabilitypage from the Admin Dashboard - Make the changes as per your site functionality
- You’re done!
FAQ
-
Q. Why should I install this plugin?
-
A. Installing this plugin is the easiest way to prevent your site from XSS Vulnerability.
-
Q. Does this plugin escape HTML in printing search?
-
A. Yes, this plugin escape HTML in
$_GETvariable which is mostly use to print the data from the URL to HTML. If your site is using$_GETthen it is safe and the HTML will be escaped otherwise you need to check. -
Q. Does this plugin has any conflict with any other plugin?
-
A. No, this plugin doesn’t have any conflict with any plugin.
Reseñas
Colaboradores y desarrolladores
"Prevent XSS Vulnerability" es un software de código abierto. Las siguientes personas han colaborado con este plugin.
Colaboradores"Prevent XSS Vulnerability" ha sido traducido a 1 idioma local. Gracias a los traductores por sus contribuciones.
Traduce "Prevent XSS Vulnerability" a tu idioma.
¿Interesado en el desarrollo?
Revisa el código , echa un vistazo al repositorio SVN o suscríbete al registro de desarrollo por RSS.
Registro de cambios
2.0.1 – Aug 19, 22
2.0.0 – Jul 14, 21
-
Bug
-
Enhancements
* Include other/extra parameters
* Fixed WPCS issues
Earlier versions
- For the changelog of earlier versions, please refer to the separate changelog.txt file.